Imagine a safe-deposit box with multiple locks. Each lock has a key that a different person holds, and the only way to open the box is to provide all the keys at the same time. Such a box can be very secure for storing your assets, provided you follow some best practices.
This is essentially what multi-signature wallets are about. Multisigs increase the security of transactions by requiring multiple parties to sign a transaction before it is executed -- a minimum number of members of the group, M-of-N, is required.
For example 2 signers out of a group of 3, or 6 of 9 signers would need to sign a transaction before it’s executed. A multisig is typically implemented as a wallet created with a smart contract that holds the group’s assets or controls the deployment of a contract.
A multisig provides enhanced security by:
- Dividing responsibility: implements separation of duties by requiring multiple owners to make decisions;
- Avoiding single point of failure: safeguards from a hacker attack or private key compromise against one party.
While the inherent constraints imposed by multisigs minimize the impact of a rogue employee, malicious attack, or lost key, they add complexity to the signing process and thus require additional security precautions over and above those of an individual wallet account. However, used correctly, multisigs can add significant security benefits and an absolute requirement for managing critical accounts.
Understanding Security Risk in a Multisig Transaction
The first step in improving security around any process is to understand the potential threats. In the security vernacular this is called threat modeling: identifying threats so we can define a mitigation strategy. We’ll walk through the multisig signing process from start to finish and highlight considerations for potential risk and threats.
The image below depicts a scenario in which six signers of a 6-of-9 contract signed a transaction using a web-browser with a wallet such as MetaMask, connected to a hardware (HW) wallet such as a Ledger. This image shows 8-steps in the process, divided into two phases: coordination and signing.
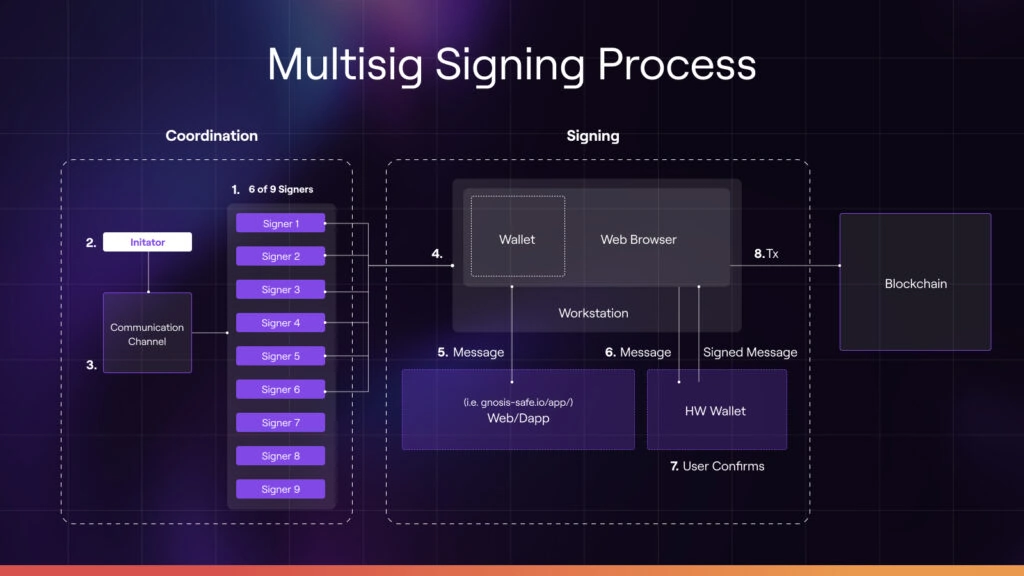
Phase 1: Coordination
Step 1 - Contract Creation & Signing Pool
This first step is the creation of the multisig contract. While every situation is unique, here are some questions to ask yourself:
- Have you considered community transparency and stakeholder disclosure when creating your contract?
- How about selecting individuals that make up the signing pool: are the individual signers trusted? How are they selected?
- Are there an appropriate number of signers to address the value of funds at stake or criticality of the contract?
- Has availability of signers been evaluated against the potential urgency of a signing event? (Too many signers can be more difficult to coordinate.)
- Does one signer hold undue sway over the others?
- Are the signers crypto literate?
- Are they security literate?
- Are sead phrases handled appropriately?
Step 2 - Initiation
Some person or entity (such as a company board or CFO office) needs to decide that a transaction is necessary. Consider the following:
- Who makes the decision to initiate a multisig transaction, and is that clear to everyone else in the pool?
- Is it a signer or a non-signer-3rd-party that initiates a transaction?
- Is it possible that a malicious or unintended bogus transaction could enter into the system?
- Who verifies that the transaction target address is valid?
Step 3 - Communication
- What communication channel is used to communicate to signers to sign a transaction (for example: email, in-person meeting, telephone, text message, etc.)?
- Is a trusted medium used?
- Can individuals be authenticated? Spoofed?
- How are signers directed to the appropriate contract or transaction (for example: with a web link)?
Phase 2: Signing
Step 4 - Initiate Signing
In the example depicted in the image above, the first 6 signers in the 6-of-9 group are signing the contract. Here they initiate this process by using their web browser to access a hosted multisig contract platform such as Gnosis Safe.
- Are the signers sure they are accessing the correct website?
- Is SSL enabled with a valid certificate?
- Could a DNS cache poison scenario impact the signing?
Step 5 - Multisig Platform Interaction
Using a web browser with a wallet extension such as MetaMask, the user can access the multisig contract within the hosted multisig platform. The initiation of a transaction involves the signer's web browser wallet receiving a message from the multisig platform. The integrity of this message is critical because this is the base of the transaction that will be signed by the user.
- Is the signer confident that the message hasn’t been tampered with?
- Does the signer trust that their operating system is free of viruses/malware?
- Are they on a trusted network?
- Can they be sure that the transaction they have initiated has not been compromised in any way?
Step 6 - Hardware Wallet
In a hot wallet scenario such as using MetaMask without a hardware wallet, MetaMask holds a user’s private keys which are used to sign a transaction. However, in our scenario, using a hardware wallet, the transaction message is sent to the hardware wallet, and the transaction can be signed with a minimal likelihood of a key disclosure. However, just like with hot wallets, the security of your private key is only as good as your ability to keep your mnemonic seed phrase used to create your keys secure.
- Are you sure you haven’t shared your seed phrase and have non-digital copy stored safely?
- Also note that, while the scenario is remote, it is not unheard of that hardware wallets have been vulnerable to wholesale compromises at the firmware level.
- Are you confident that if a specific hardware wallet wasn’t compromised, your entire multisig strategy isn’t in jeopardy?
Step 7 - Sign Transaction
Once the user sends the message to the hardware wallet, it can be signed on the hardware wallet. One drawback of hardware wallets is that they tend to have clunky minimalist screens.
- As a signer, are you sure you are signing the correct transaction?
- Are you aware that it’s possible to sign a malicious transaction?
Step 8 - Complete Transaction
Once the signed message has been returned from the user, it is sent on to the multisig smart contract. When a threshold of signers have signed the multisig, the final transaction is completed (whether it be the transfer of funds or a contract deployment).
- Are you monitoring the multisig contract so you are notified each time there is a transaction?
- If there is any unsanctioned activity on the multisig is there an incident response plan?
Mitigation Measures
Contract Creation & Signing Pool
A key objective of multisigs is to enhance security through dividing responsibilities as a means of checks and balances, as multiple parties would need to collude in order to misappropriate funds. The more parties involved reduces the risk of a single bad actor. Conversely, the complexity of coordinating a signing for a large group of signers could offset this benefit.
In general consider bigger pools for more high value assets. In the example above, a 6-of-9 could be considered a reasonable pool size for some high value treasuries, but each situation is unique. It’s also important to consider that in a decentralized organization it’s often a requirement to be transparent about any core governing process with appropriate disclosures and commitments to impartial and trusted signers.
Recommendations:
- Select the number of parties commensurate with the value of the assets.
- Use a threshold that is less than the total (M<N) so that one lost key won’t cause a disaster.
- Transparency & disclosure: determine if you need to convey organization values to stakeholders.
- Operational security: document a secure multisig process that addresses key aspects of security such as seed phrase standards, the use of hardware wallets and other considerations such as those discussed here.
Signer Security & Crypto Literacy
The nascent state of user experience in crypto and DeFi products presents a problem, and this is especially true with multisigs. The security of the process is somewhat correlated with the capability of the signers. That includes workstation security, such as up-to-date antivirus protection, and understanding how blockchain transactions work, for example verifying the right transactions are being signed.
The following recommendations should be scaled up in proportion to the size of the assets controlled by the multisig, but they provide a baseline for a secure transaction environment.
Recommendations:
- Include crypto and secure aware parties in the signing pool wherever possible.
- Provide a checklist for signing guidelines that must be followed and checked off for each signing.
- Include security awareness and phishing training.
Transaction Initiation
All the parties in the pools should be clear on how they receive direction for signing and be confident that they can validate the message sender. For example, email is easy to spoof, so an email directing all the signers to create and sign a transaction should be suspicious and this mechanism should be avoided.
Recommendations:
- Don’t publicize the identities of the signers; while security by obscurity is never considered a valid security measure on its own, for multisigs, it would be advisable to protect signers from targeted attacks, such as spear phishing where possible. Be aware that the addresses of the multisig signers could be revealed on chain, but that doesn’t necessarily disclose the owners of the signing addresses.
- Avoid associating a name, such as a .eth name with a multisig signing address.
- Details of the transaction should be clearly noted in a signing request, such as the amount, destination address and purpose.
- Signers should also have a good understanding of the purpose of transactions and the frequency to be able to better identify fraudulent transaction attempts.
- There should be a process to validate the transaction, including destination address.
Communication
Trusted communication should be used to communicate between signers.
Recommendations:
- Consider a communication channel that is harder to spoof such as a video call amongst participants or possibly some secure chat that requires multi-factor authentication for access.
- An encrypted channel such as a private VPN could be considered.
- Diligence is required to ensure that a malicious actor doesn’t compromise the communication channel to recommend a malicious transaction. If the recommender of a transaction is not a signer, then this risk is compounded.
Initiate Signing Transaction
Safe transaction signing starts with the first step.
Recommendations:
- Signers should bookmark the web page used for the signing web interface and be suspicious of links mailed to them with a link to a signing page.
- Use a trusted web application in which you believe they value security.
- Ensure the URL is correct, and that SSL is enabled to minimize the risk of accessing a malicious site.
Multisig Platform Interaction
Minimize the risk that a transaction can be compromised or altered.
Recommendations:
- Ensure proper security of your own environment/computer including up-to-date virus protection and all operating system patches up to date.
- For high value transactions a dedicated workstation would be advisable.
- Avoid signing transactions while on an untrusted network such as public WiFi.
- If using a wallet extension such as MetaMask to integrate your hardware wallet, use a trusted brand. Crypto wallets have been compromised due to weak security.
Hardware Wallet
Always use a hardware wallet, but use it wisely.
Recommendations:
- Use a hardware wallet.
- Buy hardware wallet directly from the manufacturer.
- A hot wallet should never be used for signing any critical transaction.
- Ensure private keys used for multisig signing have never been used in a hot wallet. A hardware wallet provides limited value if the private keys have already been compromised.
- Seed phrase: your security is only as good as the security of your mnemonic / seed phrase. Anyone with your seed phrase can recreate your secret keys! Never copy and paste your seed phrase or store it digitally; don’t take a picture of it or store it in a password manager. Don’t disclose it to anyone, even official customer support agents who ask. Do store it in a safe place, such as a safe deposit box. Optionally, Shamir secret-sharing (SSS) can be used to split a seed phrase into parts in which only a subset of the parts are needed to recreate the keys, such as 2 of 3 of the parts. The Trezor wallet supports SSS, and for those that don’t, a poor-man's approach to Shamir is to divide a 24 word phrase into 3 parts as follows: words 1 through 16, 8 through 24, and 16 through 8. These can be stored separately, and any two can be used to recreate the keys.
- Ensure that less than a threshold of signers is using any particular brand/model of hardware wallet to protect from a compromised hardware vendor.
- Key rotation: consider periodically updating signer keys in contract. This definitely applies if the keys have been contaminated, such as discovering that the private keys have been used in a hot wallet.
Sign Transaction
Hardware wallets typically have small screens, which can make it difficult to verify the details of a transaction.
Recommendations:
- Signers should be aware of key transaction details such as transaction amount and destination address and verify those before signing the transaction.
- Some attacks employ similar addresses, so it is important to look at more than the first 4 characters of the destination address.
Complete Transaction
A transaction completes after a threshold of signers completes the signing.
Recommendations:
- Transactions should be logged and include transaction details including the signers and who initiated the transaction.
- The multisig contract should be monitored with a tool such as Open Zepplin’s Defender to alert to any transactions on the multisig contract. Alerts should go to multiple users that are stakeholders in the contract.
- Enterprise users or high-value contracts should utilize an incident response plan to address any potential malicious activity.
Summary
These recommendations can serve as a baseline for things to consider when defining a multisig security process. Because multisigs are routinely used for large treasuries and mission critical contract deployments, the level of security strategy should be proportionate to the potential threat, whether that be a signer losing a key or a persistent state-level attack.
Minimalist Checklist
While it’s important to tailor security around the specific use case, the following checklist will serve as a very basic set of recommendations to build on:
- Communication:
- Where possible use the most secure method practical to communicate a signing event. For example, even a quick video call is an improvement over email which is easily spoofed.
- Signer Security:
- Ensure workstations are secured with up-to-date OS patches and virus protection. A dedicated signing workstation would be a wise investment for a significant account.
- Security awareness training: signers need to be extra vigilant about phishing - which might be the single biggest vector in crypto hacks.
- Hardware Wallets:
- Always use a hardware wallet.
- Ensure the private keys used in the hardware wallet have never been used in a hot wallet; if so, consider them compromised.
- Keep mnemonic/seed phrase secure; never disclose to anyone.
- Process:
- Create and document a consistent process for signing, from communication to signing on hardware wallet.
- Validate: signers should review each transaction they are signing to verify they are signing the intended transaction.
Tune into our blog and join our discord for more educational articles on the latest security standards in Web3.
Website | Twitter | Ecosystem Twitter| Developer Twitter | Studios Twitter | Telegram | Reddit | Discord| Instagram | Facebook | LinkedIn





%20(1).webp)
.webp)




.webp)
%2520(1).webp)
.webp)